Pic. 1 - Topology Diagram.
Icons designed by: Andrzej Szoblik - http://www.newo.plLet's assume that this is a new system and your colleague who's not experienced enough tried to set it up but with no success. Some work was done and the task at hand is to connect successfully the branches with headquarter accomplishing full reachability.
The first thing I'm going to do is to learn the topology diagram to know the addresses and encapsulations which connect the branches with the HQ network.
I log in to R1 and here's my first finding. Check it out:
Pic. 2 - EIGRP First Error.
The above output sent to the console indicates that R1 receives hello packets on its local S0/2 interface from the wrong address (not on common subnet). The IP address of the sender is: 172.32.14.4. R1's interface S0/2 is configured as 172.31.14.1. Clearly wrong address is assigned on R4.I jump over to R2 and correct the address on S0/2 and make sure it is EIGRP enabled by typing in a right 'network' statement.
R4 Configuration:
!
R4(config)#int s0/2
R4(config-if)#ip address 172.31.14.4 255.255.255.0
R4(config-if)#router eigrp 1
R4(config-router)#no network 172.32.0.0
R4(config-router)#network 172.31.0.0
R4(config-router)#
R4(config-if)#ip address 172.31.14.4 255.255.255.0
R4(config-if)#router eigrp 1
R4(config-router)#no network 172.32.0.0
R4(config-router)#network 172.31.0.0
R4(config-router)#
!
I perform a simple check: I want to make sure that R4's interface S0/2 is running EIGRP protocol. Here's the output:
Pic. 3 - R4's EIGRP Interfaces.
In this situation I decide to use a 'debug' tool. Be careful using 'debug' commands as they may severely impact the operation of the router. More information on how to use debug in lesson 37.
I disable a timestamps so the output of the debug is clearer. As soon as the first information is sent to the screen, I disable debug using 'u all' command (in case you are in other mode than privileged '#' the 'do u all' is used. It is the alias for: 'undebug all'. Here's what the debug reports.
Pic. 4 - Debug EIGRP Packets.
The output reveals that the local router (R4) has problems with authentication of EIGRP packets. Opcode = 5 (authentication off or key-chain missing).
The 'show key chain' shows ... zilch! There's no key chain defined on R4. I need to do it. I'm going to do to errors while configuring key chain in order to show you how they show in the 'debug ip eigrp' statement.
Here's my first erroneous configuration:
R4 Configuration:
!
R4(config)#key chain EIGRP
R4(config-keychain)#key 2
R4(config-keychain-key)#key-string cisco
R4(config-keychain-key)#
R4(config-keychain-key)#int s0/2
R4(config-if)#ip authentication mode eigrp 1 md5
R4(config-if)#ip authentication key-chain eigrp 1 EIGRP
R4(config-if)#
R4(config-keychain)#key 2
R4(config-keychain-key)#key-string cisco
R4(config-keychain-key)#
R4(config-keychain-key)#int s0/2
R4(config-if)#ip authentication mode eigrp 1 md5
R4(config-if)#ip authentication key-chain eigrp 1 EIGRP
R4(config-if)#
!
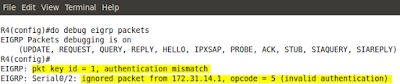
You noticed that I used the key 2. Since, the neighbor adjacency has not been built, I reach for the 'debug eigrp packets' again. Here's the output now:
Pic. 5 - Another Debug EIGRP Packets.
I check R1 and see that it uses key 1 and not key 2. The mismatch in the key number prevents the R1 and R4 from establishing adjacency.
I'll make one more mistake so that you can see another error related to authentication. Look at my key chain authentication on R4:
Pic. 6 - Running Configuration - Key Chain.
At first glance, all seems okay. But is it?Pic. 7 - Debug EIGRP Packets.
This time there is no complaints about key number, but authentication still fails. The problem is with the password used. It does NOT match with the other end. Now, displaying configuration on both R1 and R4 shows the password 'cisco'. But is it so? Check the below output on R4:Pic. 8 - Show Key Chain.
A closer inspection shows that the password cisco is followed by a 'space' character which does not show in the 'show running-config'. This a cause of the problem.
One last error that shows without any debug. Check it out:
Pic. 9 - EIGRP Unsolicited Error Message.
The problem is with the K-values used by R5's neighbor (R2). They do not match on both ends. A quick look at R5 shows that default K-values are used.Pic. 10 - Show IP Protocols on R5.
Pic. 11 - Show IP Protocols on R2.
Pic. 12 - EIGRP Configuration on R2.
R2 Configuration:
!
R2(config)#router eigrp 1
R2(config-router)#no metric weights
R2(config-router)#
R2(config-router)#no metric weights
R2(config-router)#
!
Incidentally, EIGRP unsolicited error messages are sent to the screen every few seconds which makes it hard to do the diagnostics. You can temporarily disable logging to the console 0 by typing:
R2(config)#no logging console
To bring back the defaults:
R2(config)#logging console
In the next post, I'll look at the ACLs (Access Control Lists) and how they can serve different purposes in your network.